If you deal with sensitive information, you are likely to be very cautious with your data. But not only those who deal with sensitive data want to keep their information safe, away from prying eyes. We have seen the exposure of multiple surveillance schemes. What is PRISM? Everything you need to know What is PRISM? Everything you need to know The US National Security Agency has access to the data it stores with US service providers like Google Microsoft, Yahoo and Facebook. They are also likely to monitor most of the traffic that flows through the... Read More
It's a gigantic task to understand, but it doesn't have to be that way. You can start with the documents and programs you use every day. Why WhatsApp End-to-End Encryption is a Big Deal Why WhatsApp End-to-End Encryption is a Big Deal WhatsApp recently announced that it would enable end-to-end encryption on its service But what does this mean for you? This is what you need to know about WhatsApp encryption. Read more . Some security and privacy advocates will argue that it's just not enough, but at least you can understand how to keep your Microsoft OneNote and other Microsoft Office files protected at all times.
I will explain how encryption works. How does encryption work and how is it really secure? How does encryption work, and is it really secure? Read More
Microsoft Makes Encrypting Your Files Extremely Easy 5 Effective Tools to Encrypt Your Secret Files 5 Effective Tools to Encrypt Your Secret Files We need to pay more attention than ever to encryption tools and anything designed to protect our privacy. With the right tools, keeping our data safe is easy. Read more . Really is. Go to File> Information> Protect document , and select Encrypt with password . Please enter a password. press Enter . Your file is now encrypted and will not open without the correct password.
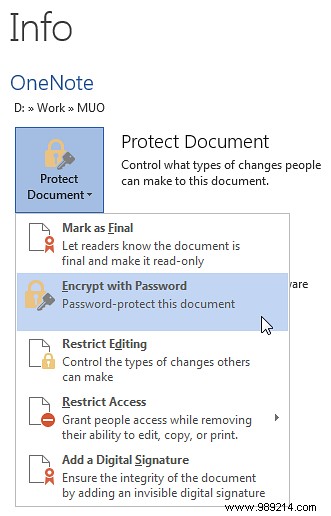
Look, that was easy, right??

Microsoft updated its de facto encryption standard for Office 2013, from a 168-bit random Triple Bit DES key implemented by Windows CAPI (Cryptographic Application Programming Interface), to the more rigorous Advanced Encryption Standard (AES), of 128-bit key, SHA1 a cryptographic hash algorithm that generates a nearly unique 160-bit key to replace plain text), and CBC (cipher block chaining).
Encryption in Microsoft OneNote works a little differently than other Office programs 7 Little-Known OneNote Features You'll Love 7 Little-Known OneNote Features You'll Love OneNote is 100% free and packed with advanced features. Let's take a look at some of the ones you may have missed. If you're not already using OneNote, these may beat you to it. Read more . Documents created in Word, Excel and PowerPoint are encrypted with a single password. In OneNote, your “documents” can be made up of many different notes, spanning different notebooks 12 Tips for Taking Better Notes with Microsoft OneNote 12 Tips for Taking Better Notes with Microsoft OneNote These 12 Tips Show You How to Take Better Notes in Microsoft OneNote. Today, digital note taking is as much about the skill as it is about the tool. Read more . Unfortunately, this makes the process of encrypting individual notebooks somewhat slow, as each must be assigned an individual password.
Of course, you can use the same password for each laptop, at your own risk. But you will still have to assign them manually.
To encrypt a notebook with a password, right-click on the desired section and select Password protect this section . A new password protection info bar will appear to the right of the app. Enter a memorable password and press OK .

If you have multiple sections of OneNote password-protected, you can lock them all using the Password Protection information bar. Right click on a section with an existing encryption password. Under All protected sections select Block all . You can also try the shortcut. CTRL + ALT + L .

Once sections of your notebook are locked, they will not be searchable until they are unlocked individually. With this in mind, please do not simultaneously lock all your notebooks to test this feature. Create a bunch of practice notebooks and lock them down. I don't want you to wade through 100+ sections, cursing me with each password entry.
Any unlocked password protection sections will be automatically locked after a set period of time, if you are not actively working on them. Obviously, this is an extremely useful security tool, but it can be annoying if you jump between sections. We can customize the lock time, as well as control the ways password protection is applied to specific sections.
Go to File> Options> Advanced. Scroll down until you see Passwords , where you will notice the three options:
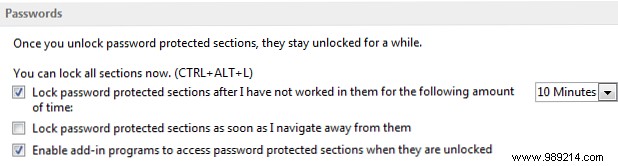
Change the block time to something that suits you. OneNote can also Lock password-protected sections as soon as I move away from them .
In a word, no . Unless you have a very specific reason to modify the encryption settings from the default, I wouldn't go there. Microsoft Office uses AES with a 128-bit key, plus SHA1 liming and block ciphers. While there is an extremely unlikely chance that your cipher could be cracked, it would take a very knowledgeable individual to complete the hack, and even then it would require 2 126.2 Computational power to recover an AES-128 key..
In other words, there is currently no practical Methods to break an AES-128 key.
That said, if you really want to scramble, you can use the Office Customization Tool, which also has a relatively comprehensive reference page for you to peruse. I won't give detailed instructions on how to use the OCT, as it really would be better to leave the encryption settings alone, but I can't deny the whims of those who want to tinker.
I would suggest setting up a virtual machine. What is a virtual machine? Everything you need to know What is a virtual machine? Everything you need to know Virtual machines allow you to run other operating systems on your existing computer. This is what you should know about them. Read More
The encryption offered by Microsoft Office is strong. AES is unlikely to be broken in the extremely immediate future, and if it is, the computational requirements will be extremely high, beyond the reach of the usual cybercriminals.
But that doesn't mean you can be complacent. You are more likely to accidentally introduce a malicious entity into your network, allowing access to sensitive information from inside the gates. With this in mind, consider where that email came from, or just who you're sending a file to, and you won't be the weak security liaison being cursed at at the office.
Do you use Microsoft Office's built-in encryption? Or do you use an external tool? How do you manage your password-protected OneNote sections?